How it works
To start automating code security reviews, create an account and workspace on the Pensar Console.During onboarding you will be prompted to connect to GitHub or GitLab. You will then be guided through the process of connecting a repository to the Pensar Console.The steps below will guide you through adding a project after workspace creation/onboarding.
Check out our quickstart guide if you are having trouble or reach out to us at [email protected].
Check out our quickstart guide if you are having trouble or reach out to us at [email protected].
1
Connect repository
Connect your repository to the Pensar Console to start running security scans on your codebase.Ensure you have either connected GitHub or GitLab in order to view your repositories in the Pensar Console. [TODO: add links]To add a repository, naviagte to the 
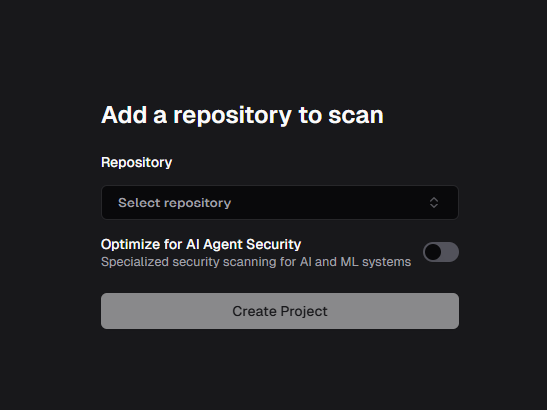
Add repository button located at the top of the left sidebar.

If you would like Pensar to scan for AI agent related security issues as well, check the
Optimize for AI Agent Security toggle. This will enable the AI Agent Security Framework by default on that project/repository. This can be changed later in project settings.2
Configure project
Pensar will then gather context on your repository including parsing the readme, detecting languages used, the use case of the application, what libraries or dependencies are used, etc.You will be prompted to accept or make edits to the description of your project that our system has extracted. This aids in tuning the Pensar agent to focus on security issues specific to your repository and application and helps to filter out false positives that may arise.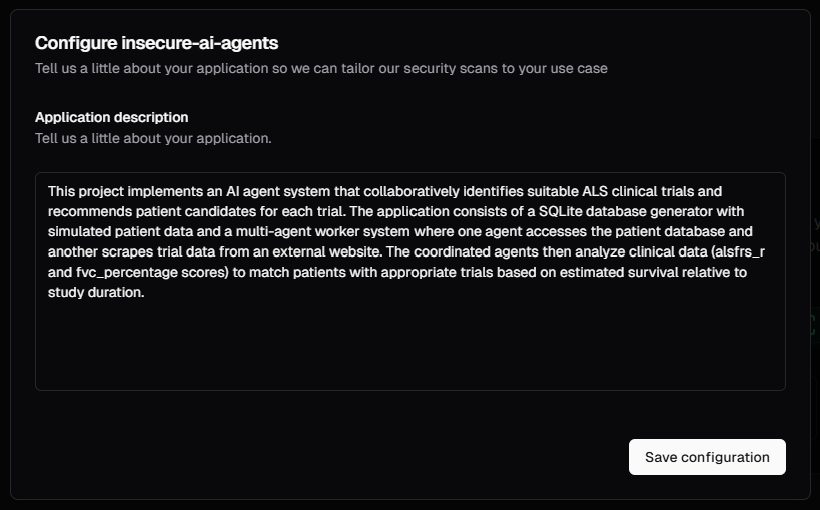
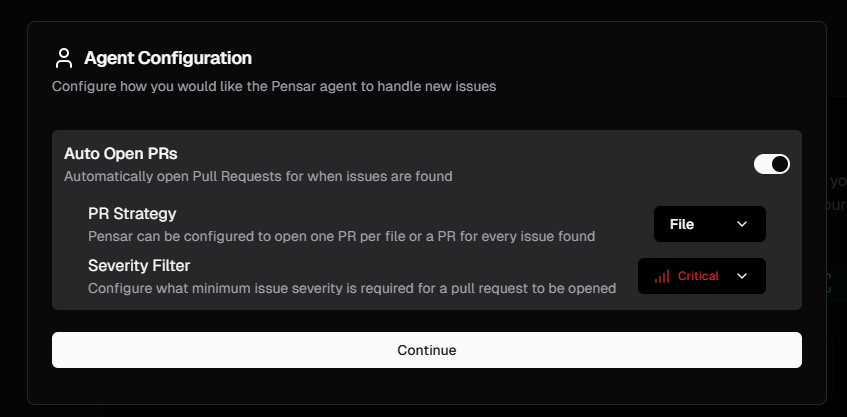
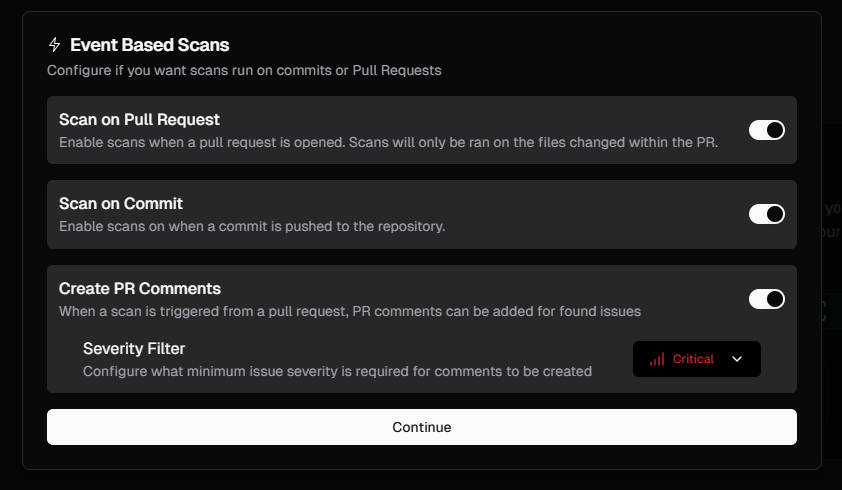

You have the option for auto-pull-requests to be submitted on a per-file or per-issue basis.Enabling per-file submissions will combine auto-generated patches into a single pull-request for each vulnerability found in a file. For instance, if a file has 3 critical vulnerabilities, Pensar will combine the patches for each vulnerability and submit a single pull request to fix all three issues.Per-issue pull request submissions will submit a single pull request with a patch for each individual vulnerability detected. Following the above example, three pull requests will be opened each containing a patch to a single critical vulnerability.
Pull requests will trigger GitHub notifications if they are enabled in GitHub.


You may configure whether Pensar automatically adds comments with change suggestions that contain auto-generated security patches for vulnerabilities found in the target pull request and likewise set a miniumun severity fitler to tune this behavior.
3
Launch scan
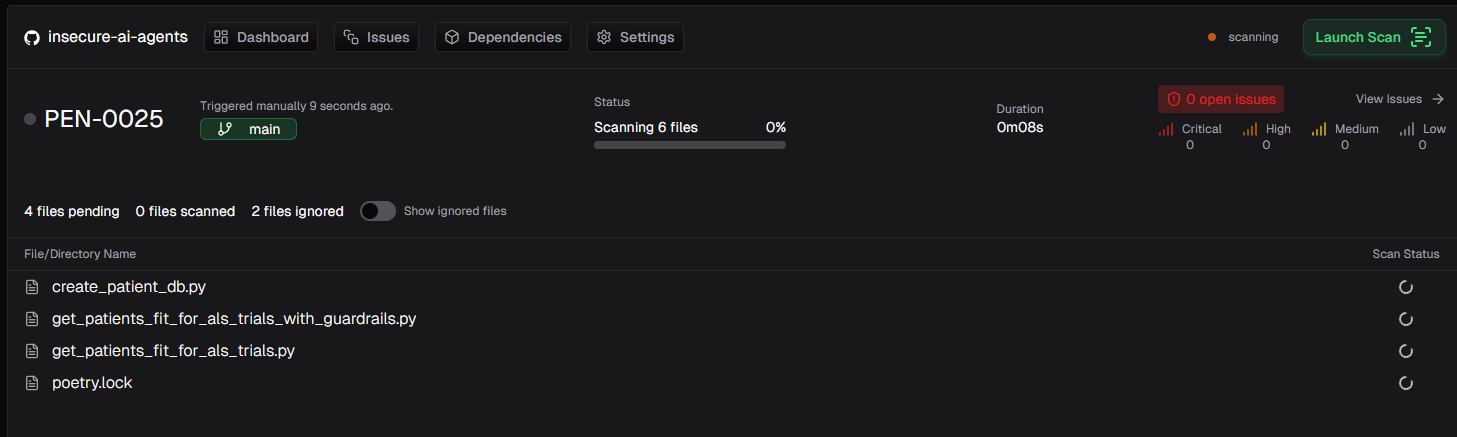
It’s time to launch a scan! Manually launching a scan will trigger a full codebase security review by Pensar.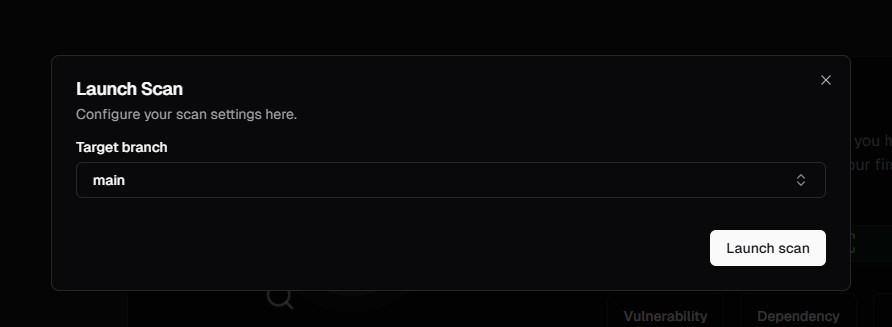


How does the Pensar AI Agent access my code?
We temporarily clone your repository into a secure containerized runtime in AWS. After scanning is complete, this temporary clone is deleted from the container’s filesystem completely. The only data we store are:- Vulnerabilities found
- A diff that represents the changes to apply to the codebase to patch a vulnerability (i.e. the diff representation of our auto-generated security patch).
All data is encrypted in-transit and at-rest.